Huntress : Configuring the "Usage Location" of an identity in Microsoft Entra ID
Huntress detected one or more identity logins without a Usage Location. The Usage Location is set within Microsoft Entra ID settings. Huntress utilizes this location to identify where the identity should be logging in from following a normal pattern of behavior.
You need to set the Usage Location in Microsoft for these identities. Huntress has provided a knowledgebase article with instructions. When complete, resolve this escalation. You can resolve for all below or individually for each identity lower down the page.
Huntress MDR for Microsoft 365 utilizes the Microsot Entra ID Usage Location setting as part of the Unwanted Access feature. The Microsoft Entra ID Usage Location value is used to determine the country a given user will be operating from. This setting might affect license availability, feature availability, data center location, and data governance. It is a field that should be present on all user identities, but in many cases Huntress has observed this field to be empty. This article will provide resources on setting this field appropriately to ensure compatibility with the Unwanted Access feature.
WARNING: Setting or changing the Usage Location parameter for an identity might impact the assigned license and available features for that identity. Double check the correct Usage Location is being applied to correct identity before making any changes.
There are three methods of configuring Usage Location discussed in this article:
1via the UI in the Azure Portal, best for a small number of individual user changes
2via the PowerShell Graph SDK, best for bulk operations where all users are in the same country
3via Entra Connect, the Directory Synchronization tool, best for users of this software
Configuring Usage Location using the Azure Portal
This scenario works best for single or a small amount of users needing modification.
- Login to https://portal.azure.com/ with sufficiently privileged account that is able to modify user objects. (e.g. Global Administrator, User Administrator)
- Navigate to the Microsoft Entra ID module.
- Navigate to the individual user you wish to update by clicking on their name in the list of all users.
- Click the "Edit Properties" item in the ribbon in the upper left of the Overview page.
- Click the Settings option at the top of the user properties page and choose the appropriate Usage Location from the drop down.
- Once a suitable Usage Location is chosen, United States in this example, be sure to click the Save button at the bottom of the open menu.
Configuring Usage Location using PowerShell
This scenario works best for bulk operations when many users do not have a Usage Location set. The procedure outlined here will set ALL users without a Usage Location to the SAME specified value.
This article describes using the Microsoft PowerShell Graph SDK to perform these changes. We recommend this method for admins that have experience utilizing this module to perform Microsoft 365/Entra administrator tasks. Additionally, while these operations can be completed using the deprecated Azure AD and MSOnline PowerShell modules, Huntress support is unable to provide guidance for this legacy module. We recommend all administrators follow Microsoft's guidance and migrate to the new Graph SDK linked above.
- Connect to the Microsoft Graph service using the following command:
Connect-MgGraph -Scopes "User.ReadWrite.All"
(other scopes, such as Directory.ReadWrite.All will also work.)
If this is the first time you've used the PowerShell Graph SDK, you will be required to complete the Application Consent dialog before proceeding.
- Run an exploratory command to show the list of ALL users within the tenant that do not have a value set for Usage Location. These will be the users modified in the next step. Double check the list to verify accuracy.
Get-MgUser -All -Property Id,UserPrincipalName,UsageLocation | Where-Object {$_.UsageLocation -eq $null} | Sort UserPrincipalName | ft Id,UserPrincipalName,UsageLocation
The next step is the point of no return. The command included in the next step will commit changes to your live environment. As this command writes over empty usageLocation values, and this field is "non-nullable," they cannot be cleared after these changes are made. Don't worry if you set the wrong location as you are able to modify it to the correct location if needed!
- Use the following command to set all users within the tenant that do not have a usage location to now have a usage location that you specify. The usage location should be the two character ISO 3166 country code. (e.g. US = United States, AU = Australia, GB = United Kingdom/Great Britain) In the below code block, replace <COUNTRY_CODE> with your desired value.
Get-MgUser -All -Property Id,UserPrincipalName,UsageLocation | Where-Object {$_.UsageLocation -eq $null} | ForEach-Object {Update-MgUser -UserId $_.Id -UsageLocation "<COUNTRY_CODE>"} - Run the same exploratory command from Step 2 and verify no results are returned. A return of no results indicates you have no users within your tenant that have a null Usage Location value.
Additional information about the commands used and other possible conditions of altering this value can be found in this Microsoft support article.
Connect-MgGraph -Scopes "User.ReadWrite.All"(other scopes, such as Directory.ReadWrite.All will also work.)
Get-MgUser -All -Property Id,UserPrincipalName,UsageLocation | Where-Object {$_.UsageLocation -eq $null} | Sort UserPrincipalName | ft Id,UserPrincipalName,UsageLocationGet-MgUser -All -Property Id,UserPrincipalName,UsageLocation | Where-Object {$_.UsageLocation -eq $null} | ForEach-Object {Update-MgUser -UserId $_.Id -UsageLocation "<COUNTRY_CODE>"}Usage Location considerations for Microsoft Entra Connect
Microsoft Entra Connect was formerly known as Azure AD Connect, Azure AD Sync, and DirSync.
Depending on when Entra Connect, or any of the previously named versions, was installed in an environment and whether or not that environment originally had an on-premises Microsoft Exchange deployment can affect what property is being synchronized from the on-premises Active Directory environment to Entra ID. By default, the synchronization utility used the msExchUsageLocation attribute to determine the value for usageLocation in Entra ID, but this attribute is not present in an Active Directory environment without the schema extended for Microsoft Exchange. While this was recommended at one time, it is no longer advisable to extend the Active Directory schema to include Microsoft Exchange attributes if there is no intention to run on-premises Microsoft Exchange.
In order to ensure proper population of the usageLocation attribute in both the on-premises Active Directory and Entra ID environments, it's recommend to configure the synchronization rules to populate the Entra ID usageLocation attribute parameter based on the c attribute within Active Directory. Once this rule is configured the user's location will be set based on the Country chosen in the Address tab of Active Directory Users & Computers. The procedure to configure this in a default setup environment is shown below.
There are a variety of considerations needed when attempting these changes in an environment where an on-premises Active Directory is being synced with Entra ID. This article cannot encompass every possible syncing configuration, but it aims to provide concepts and guidance. As a result, Huntress support might not be able to assist in all Directory Synchronization scenarios due to the complex nature of some environments. Before making any changes to a directory synchronization deployment be cognizant of any undesired the effects changes will have.
Scroll to the bottom of the list and make note of the highest "precedence" number in the list. In our example it is 153.
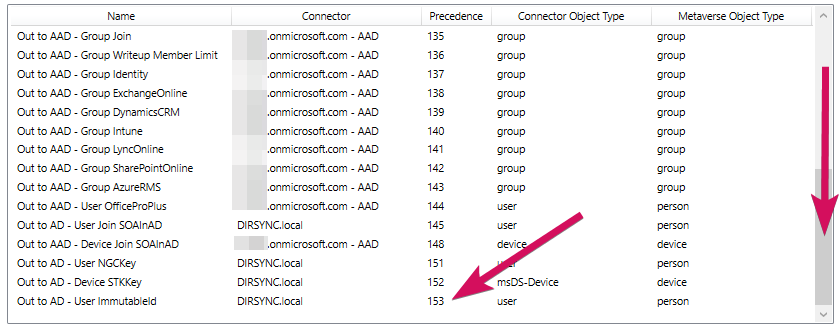
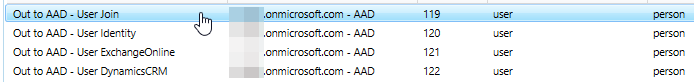
Scroll back to the top of the list and click on the "Out to AAD - User Join" option on the list and then select the "EDIT" button at the bottom of the list.
Note: The remote environment's domain will be displayed instead of the ".onmicrosoft.com" domain shown here.
The following dialog will be presented, select Yes.
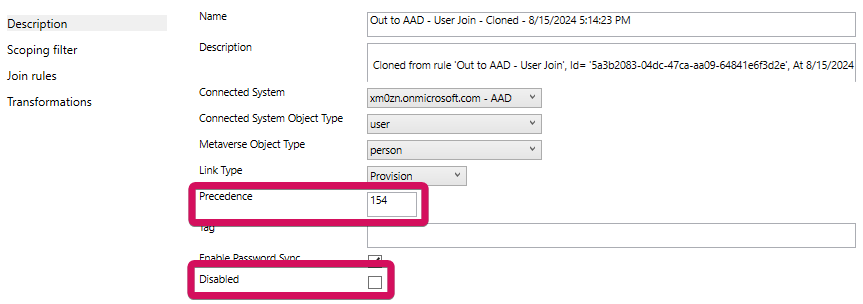
Click on the "Transformations" option on the left, scroll down until you can see usageLocation in the list of transformations.
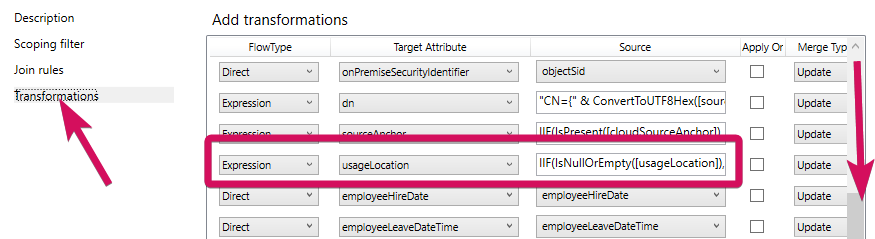
Edit the Source field for the Expression FlowType for the usageLocation Target Attribute. By default, the Source field, should read as:IIF(IsNullOrEmpty([usageLocation]),IgnoreThisFlow,[usageLocation])
The above expression will vary depending on various criteria. Changing it to the below value will have the desired effect if the Country/region field in Active Directory is populated as shown in the final step. It's recommended to copy and paste the existing Source field information to somewhere safe (e.g. a Notepad document) in case it needs to be reverted or used for future reference.
This value should be changed to the following:IIF(IsNullOrEmpty([c]),IgnoreThisFlow,[c])
This expression operates as an if-else statement using the following format, "IIF(condition, true_value, false_value)".
In plain English, the changes above say, "If the local attribute c is blank, do nothing, if it is populated then use the value for c as usageLocation in Entra ID for outbound synchronization tasks." The Expression FlowType is preferred over a Direct as this prevents conflicts with locally unset values interfering with values that might be set in Entra ID.
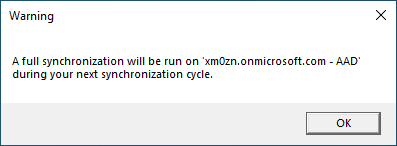
Once the above value is changed, click the Save button at the bottom of the dialog box. If everything is correct, the following dialog will be displayed. Click OK.
IIF(IsNullOrEmpty([usageLocation]),IgnoreThisFlow,[usageLocation])
The above expression will vary depending on various criteria. Changing it to the below value will have the desired effect if the Country/region field in Active Directory is populated as shown in the final step. It's recommended to copy and paste the existing Source field information to somewhere safe (e.g. a Notepad document) in case it needs to be reverted or used for future reference.
This value should be changed to the following:
IIF(IsNullOrEmpty([c]),IgnoreThisFlow,[c])This expression operates as an if-else statement using the following format, "IIF(condition, true_value, false_value)".
In plain English, the changes above say, "If the local attribute c is blank, do nothing, if it is populated then use the value for c as usageLocation in Entra ID for outbound synchronization tasks." The Expression FlowType is preferred over a Direct as this prevents conflicts with locally unset values interfering with values that might be set in Entra ID.
Once the above value is changed, click the Save button at the bottom of the dialog box. If everything is correct, the following dialog will be displayed. Click OK.
Start-ADSyncSyncCycle -PolicyType DeltaIn order for the changes above to take effect, the "Country" field must be set on the "Address" tab for a user in Active Directory. An example of a user set to United States is shown below. These values can also be set in bulk using the PowerShell cmdlet Set-ADUser.
Related Articles
Huntress Alert: Login from Unexpected Country
Login from Unexpected Country If alert trigger for "Login from unexpected country" from select the alert in dashboard. In scope section, we may select it for all organization or for particular organization. Steps to Resolve There are two ways to ...